Abap bitwise operations
You forgot to provide an Email Address. This email address is already registered. You have exceeded the maximum character limit. Please provide a Corporate E-mail Address. By submitting my Email address I confirm that I have read and accepted the Terms of Use and Declaration of Consent. By submitting your personal information, you agree that TechTarget and its partners may contact you regarding relevant content, products and special offers.
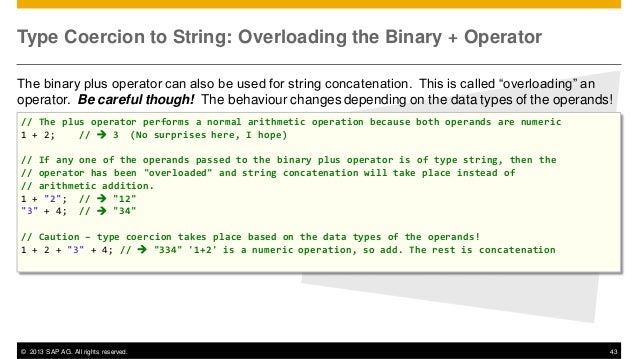
You also agree that your personal information may be transferred and processed in the United States, and that you have read and agree to the Terms of Use and the Privacy Policy. In addition, you'll learn how to use ABAP bitwise operators to write Boolean algebraic expressions. Advanced ABAP operations with elementary data types Working with ABAP date and time data types Understanding ABAP programming bits and bytes.
Modern programming languages do such a tremendous job of abstracting the complexities of computer architectures that, these days, we seldom have any need to work at the bits and bytes level.
Normally, whenever we talk about the built-in native data types provided in the ABAP programming language, we focus our attention around the numeric and character data types. However, ABAP also provides a hexadecimal data type X that is used to represent individual bytes in memory. The values stored in the individual bytes are represented as two-digit hexadecimal numbers. If you have never worked with binary or hexadecimal numbers before, then a brief introduction is in order.
A byte is a unit of measure for memory inside of a computer. Each byte is comprised of 8 bits. The term bit is an abbreviation for binary digit. A bit can have one of two logical values: In terms of computer circuitry, bits that have the value 1 are turned on, while those that have the value 0 are turned off.
The binary or base-2 number system represents numeric values using binary digits. As you can see, reading from right to left, the value of each bit is calculated by multiplying one or zero i. Therefore, the values of bytes are often represented using the hexadecimal or base numbering system. Conveniently, each hexadecimal digit can hold any possible value of 4 bits commonly called a nibble. Therefore, two hexadecimal digits can be used to represent a single byte of information in memory.
Here, as is the case with the C and STRING data types described in Chapter 1, String Processing Techniques, there is a trade-off between performance and flexibility. The following sections describe the built-in bitwise operators available in ABAP.
You can use the GET BIT and SET BIT statements to read and write individual bits of a hexadecimal data object. The general syntax of these statements is shown in Listing 2. For good measure, we also shift the bits around one more time at the end of the code snippet, using the SHIFT statement in byte mode.
However, there are situations where it can be quite useful. One way other modern programming languages, such as Java or. NET, get around this limitation is by developing a so-called numeric wrapper class. For instance, the java. BigInteger class provided with the Java 2 SDK is used to represent arbitrarily large integer values. In addition to the GET BIT and SET BIT statements, ABAP also provides a series of bitwise logical operators that can be used to build Boolean algebraic expressions.
Of course, even if you have worked with Boolean operators before, you might need a bit of a refresher. Just like normal arithmetic operators, the bitwise operators can be combined in complex expressions using parentheses, and so on. To see the power of bitwise operators such as the ones listed in Table 2. Imagine that you are tasked with building a custom document management system.
One of the requirements of this system is to be able to assign rights permissions to the individual documents maintained in the system.
ABAP bit shifting and bitwise add, subtract, multiply · GitHub
One way to store these assignments might be to create a database table that contained a series of flag columns to indicate whether or not a user had a particular permission for a given document. Unfortunately, there are a couple of problems with this approach.
First of all, it requires that we create separate fields for each possible permission type.
As the system grows, additional permission types require a modification to the database table. This phenomenon leads into the second problem — namely, space. In other words, each additional flag column adds another byte or two of storage to every row in the table. Of course, another option is to capture the permissions in separate rows.
Still, either way you slice it, this can get expensive from a storage perspective. Instead of creating a new flag column each time we want to add a new permission type to our system, what if we could figure out a way to store a bunch of Boolean flags in a single field?
Naturally, the hexadecimal data type lends itself well to this kind of storage operation because it can be used as a type of bit mask to represent a large number of flags at the bit level.
For example, a single byte bit mask could represent up to 28, or , possible values, leaving us plenty of room to grow. The values of the individual Boolean flags can then be set using bitwise operators. Collectively, the process of representing a series of flags at the bit level and manipulating those flags using bitwise operators is referred to as bit masking.
ABAP COMPUTE BIT Statement syntax and functionality in SAP
The code excerpt in Listing 2. These permission values are assigned to a display-only user using the BIT-OR operator, which effectively works like an addition operator in this case. We can then confirm whether or not the user has a given permission by applying the BIT-AND operator.
Understanding ABAP programming bits and bytes
Here, the result matches the permission constant bit-for-bit if the particular permission has been assigned. This can be confirmed by using the equality operator in an IF statement. In the example, the user has Display permissions but not Create permissions. As you can see, bit masking can be used as an effective compression technique. Other practical examples of bit masking include the storage of user preferences and set operations, which are described in an example in the online SAP Help Portal.
In this chapter, you learned about some advanced and perhaps lesser-known features of elementary data types in ABAP. In the next chapter, we mix things up a bit and take a look at dynamic programming in ABAP. This excerpt from ABAP Cookbook: Download a PDF of this chapter.
Critical essentials of a SAP HANA big data strategy. By submitting you agree to receive email from TechTarget and its partners.
If you reside outside of the United States, you consent to having your personal data transferred to and processed in the United States. Stratasys' new Continuous Build 3D Demonstrator printer technology aims to grow 3D printing in manufacturing with a Vendor claims new technique provides faster, more flexible production and will help make 3D printing an integral part of the Given the exploding industrial internet of things market, surveying the choices can be overwhelming.
To get you started, here's a It's time to stop worrying and embrace the Oracle cloud, at least in a hybrid environment that integrates cloud and on-premises Oracle's Multitenant technology enables users to plug multiple databases into a single container database.
Is it time for your IBM pulled the plug on its distribution of Hadoop in favor of reselling Hortonworks' bundle of big data technologies, a decision Moving relational data into Hadoop is not a slam dunk. To avert programming complexities, a major Texas school turned to As companies collect customer data and other types of information from more and more sources, the master data management process Mobile app users want a consistent experience for all apps -- on all devices.
AWS Device Farm tests application features but In this chapter excerpt from Serverless Architectures on AWS, author Peter Sbarski shares five tricks developers can use to While much of the developer community turns to Kubernetes to schedule containers, open source AWS Blox could carve out a niche The world's top tech companies are currently the biggest users of deep learning applications, but more typical enterprises may be Lenovo and Autodesk are two organizations that are increasing their use of the cloud for analytics applications, looking to lower When deploying deep learning models into production, experts say it's important to take care of the basics, like model design and Sprint CMO Roger Sole shares his company's reboot story and explains how technology is radically changing his department's Large enterprise customers demonstrate novel uses of Pegasystems' CRM platform for business process management as Pega leadership While the technology of customer data mining continuously improves, organizations still need the human factor of customizing As companies struggle with BI integration, Microsoft has figured out the magic formula with its Power BI dashboard.
Adobe rounds out its cloud suite with Adobe Scan, which allows mobile employees to capture documents and images and turn them SQL Server has made 5 key improvements that can help integrate AI capabilities and analytics into the enterprise more After forming a new joint venture, LifeWorks, HCM vendor Ceridian uses LifeWorks' employee recognition, engagement and perks Choose your talent management system wisely or risk irking your employees.
Learn the criteria for evaluating software that HCM systems for big employers are increasingly in SaaS form and incorporating a wide range of HR tech beyond core functions, such All Rights Reserved, Copyright - , TechTarget. Techtarget Network News Features Tips More Content Answers Buyer's Guides Essential Guides Opinions Photo Stories Podcasts Quizzes Tutorials Sponsored Communities. SAP ABAP SAP interface technologies SAP Java and J2EE SAP Web applications SAP Workflow All Subtopics.
Manage Learn to apply best practices and optimize your operations. Share this item with your network: Sign in for existing members. Continue Reading This Article Enjoy this article as well as all of our content, including E-Guides, news, tips and more.
Step 2 of Copyright Info This excerpt from ABAP Cookbook: This was last published in November Dig Deeper on SAP ABAP All News Get Started Evaluate Manage Problem Solve.
CAST report uncovers problems in customizing SAP applications SAP asks for help with enterprise Web 2. What SAP says about ABAP's future Load More View All News. Choosing between BSP and Web Dynpro ABAP jobs and more: Implementing modern practices in an ABAP development shop SAP ABAP programming needs to be brought into the modern era Introduction to SAP ABAP internal tables Introduction to SAP ABAP internal tables Load More View All Manage. Add My Comment Register. Login Forgot your password? Submit your e-mail address below.
We'll send you an email containing your password. Your password has been sent to: Please create a username to comment. Latest TechTarget resources Manufacturing ERP Oracle Data Management AWS Business Analytics CRM Content Management Financial Applications Search Manufacturing ERP New 3D printer technology could be a boon to production efficiency Stratasys' new Continuous Build 3D Demonstrator printer technology aims to grow 3D printing in manufacturing with a Carbon displays new additive manufacturing technology Vendor claims new technique provides faster, more flexible production and will help make 3D printing an integral part of the Three promising IIoT platform options aim to improve manufacturing Given the exploding industrial internet of things market, surveying the choices can be overwhelming.
Search Oracle MySQL Community Server vs. Oracle MySQL databases It can be confusing to select an Oracle MySQL database. Which one makes sense for you? Time to embrace, capitalize on an Oracle hybrid cloud It's time to stop worrying and embrace the Oracle cloud, at least in a hybrid environment that integrates cloud and on-premises Five reasons to migrate to an Oracle Multitenant architecture Oracle's Multitenant technology enables users to plug multiple databases into a single container database.
Search Data Management IBM bets on Hortonworks Hadoop platform as its big data engine IBM pulled the plug on its distribution of Hadoop in favor of reselling Hortonworks' bundle of big data technologies, a decision High-level tools help Hadoop data lake go to school Moving relational data into Hadoop is not a slam dunk.
Blooming of master data sources complicates customer MDM efforts As companies collect customer data and other types of information from more and more sources, the master data management process Search AWS AWS Device Farm testing doesn't give full performance picture Mobile app users want a consistent experience for all apps -- on all devices. Strategies to accelerate AWS Lambda functions In this chapter excerpt from Serverless Architectures on AWS, author Peter Sbarski shares five tricks developers can use to AWS Blox enters crowded open source container market amid skepticism While much of the developer community turns to Kubernetes to schedule containers, open source AWS Blox could carve out a niche Search Business Analytics How enterprises can find the right deep learning use cases The world's top tech companies are currently the biggest users of deep learning applications, but more typical enterprises may be Cloud data analytics gets a higher profile in companies Lenovo and Autodesk are two organizations that are increasing their use of the cloud for analytics applications, looking to lower Experts explain how to deploy deep learning in production When deploying deep learning models into production, experts say it's important to take care of the basics, like model design and Search CRM CRM, martech stack helping customers hear Sprint now Sprint CMO Roger Sole shares his company's reboot story and explains how technology is radically changing his department's CRM AI is the top topic at PegaWorld Large enterprise customers demonstrate novel uses of Pegasystems' CRM platform for business process management as Pega leadership Customer analytics techniques boost sales and service strategies While the technology of customer data mining continuously improves, organizations still need the human factor of customizing Search Content Management Three BI dashboard best practices you need to know As companies struggle with BI integration, Microsoft has figured out the magic formula with its Power BI dashboard.
Adobe Document Cloud adds mobile scan, upgrades e-signature software Adobe rounds out its cloud suite with Adobe Scan, which allows mobile employees to capture documents and images and turn them Five SQL improvements you need to know about SQL Server has made 5 key improvements that can help integrate AI capabilities and analytics into the enterprise more Search Financial Applications Ceridian uses employee engagement tool from its own joint venture After forming a new joint venture, LifeWorks, HCM vendor Ceridian uses LifeWorks' employee recognition, engagement and perks Evaluate HR technology to fit your talent management processes Choose your talent management system wisely or risk irking your employees.
SaaS HR software dominates as cloud HCM systems proliferate HCM systems for big employers are increasingly in SaaS form and incorporating a wide range of HR tech beyond core functions, such About Us Meet The Editors Contact Us Privacy Policy Advertisers Business Partners Media Kit Corporate Site Contributors Reprints Archive Site Map Answers E-Products Events Features Guides Opinions Photo Stories Quizzes Tips Tutorials Videos.
Unary operator that flips all of the bits in the hexadecimal number to the opposite value. For example, applying this operator to a hexadecimal number having the bit-level value e. Binary operator that compares each field bit-by-bit using the Boolean AND operator. Binary operator that compares each field bit-by-bit using the Boolean XOR or eXclusive OR operator.
Binary operator that compares each field bit-by-bit using the Boolean OR operator.